
Cybersecurity News
The US Government Failed Their Cybersecurity Audit. Now What?
From NASA to the State Department, federal agencies are relying on outdated systems, ignoring mandatory security patches and failing to protect classified data.
Stay updated with all the latest news and announcements

Cybersecurity News
From NASA to the State Department, federal agencies are relying on outdated systems, ignoring mandatory security patches and failing to protect classified data.

Cybersecurity Trends
Today, over 95% of businesses utilize cloud computing. At the same time, companies often lack proper security protocols to manage this rapidly developing digital landscape.

Cybersecurity News
In what is considered to be the largest ransomware attack in history, a group of hackers have compromised at least 1000 companies in a stunning Fourth of July attack.

Cybersecurity Trends
With new buzzwords being generated on a seemingly constant basis, it can be difficult to distinguish between passing fads and emerging trends.

Cybersecurity News
While the recent attacks on the JBS plants and the Colonial Pipeline are far from unique, the tangible nature of the damage hits close to home.

Cybersecurity Trends
As Attack Surface Management (ASM) begins to gain traction, here are the top four reasons why it may be the right fit for your organization.

Cybersecurity News
SmileDirectClub, a celebrated tele-dentistry company, just lost over 15% of their market value in under 15 minutes. The cause? A cyber security breach from two weeks ago.

Guest Post
When you receive a call on your phone from an unknown number, it's nearly impossible to guess who's calling. Increasingly, it could be someone vishing you.

Cybersecurity News
The Biden Administration has announced plans to launch a '100-day sprint' to shore up the US power grid against cyber-attacks.

Cybersecurity News
In the wake of the SolarWinds and Microsoft attacks, the UN has released a landmark cybersecurity report that's been two years in the making. Here's what you need to know.

Cybersecurity Alert
Since January '21, hackers have been exploiting multiple vulnerabilities in Microsoft Exchange Server to infiltrate a broad range of systems. Here's what you need to know.
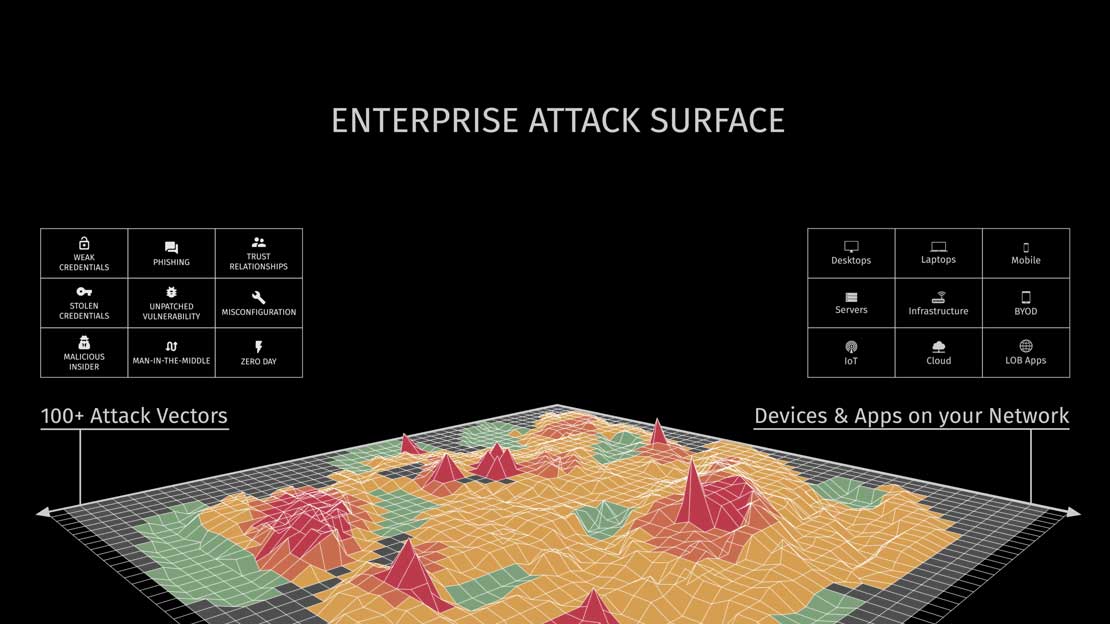
Cybersecurity Trends
Unfortunately, organizations across nearly every sector are still struggling to secure their public-facing applications.

Cybersecurity News
On Friday, February 5, a hacker breached the water plant serving Oldsmar, Florida and instructed it to increase the amount of lye in the water to extremely dangerous levels.

Cybersecurity News
Over the last few years, adoption rates of rival messaging apps, Signal and Telegram, have skyrocketed, placing WhatsApp's dominance into question.
Cybersecurity Trends
197. That's how many days it takes an average company to detect a security breach. Hackers have over 6 months before their victim is even aware that they've been hacked.

Cybersecurity Trends
It's fair to say that 2020 held some unique challenges, but 2021 will have its own hurdles. These are the top five challenges facing CISOs as we move into the new year.

Cybersecurity News
A highly sophisticated actor has taken advantage of SolarWinds security flaws to infiltrate governments and businesses around the world. Here's what you need to know.

Never Trust, Always Verify
Chris Krebs, the former Director of CISA, was fired on November 17th after repeatedly affirming that the 2020 election was the "most secure in American history."

Cybersecurity News
Following repeated penalties for state-sponsored doping, Russia was finally banned from all Olympic sports for 4 years. Have they retaliated by hacking the games themselves?
Silent Breach in the press
announcement
Silent Breach in the press
© Copyright Silent Breach. All Rights Reserved.