Social Engineering
Putting people at the heart of cybersecurity.
The Human Touch
While social engineering has been around for decades, recent years have registered a concerning uptick in the quantity and quality of social attacks.
Using simple, yet effective techniques, Silent Breach ethical hackers have found that a layered attack — combining phishing, vishing, as well as targeted spearphishing attacks — can critically breach 90% of businesses within one week, all without writing a single line of code.
The reality is that it's far easier (and cheaper) to fool people than it is to fool a machine.
Consequently, it has become increasingly clear that the largest cybersecurity threat to nearly any organization is its people.

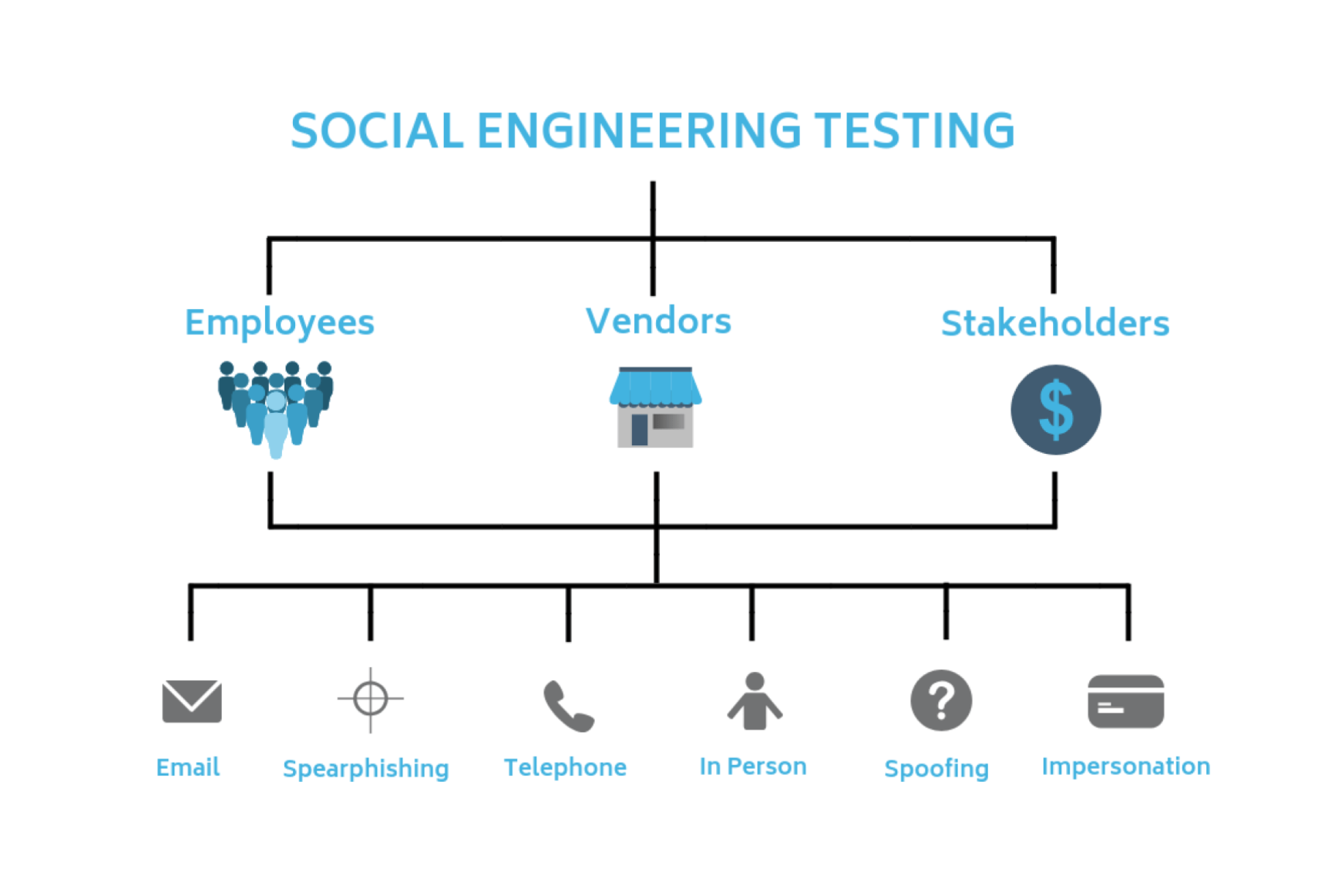
Preparation Is The Best Defense
Silent Breach offers comprehensive, realistic, and fully customizable social engineering simulations.
Our award-winning experts are trained in both social psychology as well as tactical cybersecurity, to ensure that you'll be prepared against the very best social hackers.
Information security cannot be left to a set of regulations or handed off to a security department. To be effective, it must lead to a transformation in organizational priorities and culture.
A social engineering campaign is the best way to determine your current baseline and help set your priotities going forward.
Contact us today for a same-day custom quote.
Our Social Engineering Solutions
Email Phishing
The first line of attack. Phishing emails seek to convince the recipient that a malicious email is legitimate; usually leading to the user downloading malicious payload, making a payment, or exposing credentials.
Phone Vishing
Vishing is similar to phishing, but differs in its mode of execution. Instead of using email, vishers contact their targets by phone, often conveying a sense of urgency, authority, or pity towards some malicious goal.
Spearphishing
Spearphishing has become extremely popular over the last several years. Due to the prevalance of social media, hackers can now design extremely detailed campaigns in a relatively short amount of time.
USB Drops
Many breaches, including the 2010 Stuxnet worm, have been initiated via malicious USB flash drives. Often, USBs are dropped in a company parking lot or cafeteria in the hopes of someone finding and plugging it into their computer.
Physical Access
A Silent Breach mole attempts to physically access restricted zones by tailgating legitimate employees, impersonating an external partner, or overriding physical security measures (such as scaling a fence or picking a lock).
Decoy Landing Pages
Phishing campaigns can be supplemented with decoy landing pages that are exact replicas of your organization's website or a recognized service (Outlook, Salesforce, etc.) depending on the campaign goals.
Tactical Training
All Silent Breach trainers are seasoned security experts, with extensive experience in training in the public, private and military world. Silent Breach offers on-site or virtual workshops designed to respond to the latest threats.
Smishing
An updated version of phishing, smishing occurs via SMS or other text messaging platform like WhatsApp or Facebook. As users learn to handle emails carefully, texting has become the new battleground for social hackers.
© Copyright Silent Breach. All Rights Reserved.