Quantum Cloud
Cloud Monitoring and Auditing
Cloud Security Made Simple
Security misconfigurations continue to be the most commonly identified vulnerabilities during Silent Breach penetration testing exercises.
As more businesses transition to the cloud, it comes as no surprise that securing your cloud instance should be a top organizational priority. However, along with the plethora of available features that cloud providers are only too eager to bill you for, the complexity of fine-tuning your cloud instance only continues to grow.
Here's where Quantum Armor comes in. Utilizing a range of proprietary algorithms, Quantum Armor helps you monitor, audit, and harden your cloud instance without installing any agents. This is done by leveraging the APIs that are already in place and provided by the cloud vendors themselves. Additionally, cloud security controls, metrics, and logs can be monitored on a daily basis to spot any suspicious activity or potential attacks.
Furthermore, while cloud providers offer secure infrastructure that is ISO 27001 or SOC2 compliant, they take no responsibility for the security of the data or applications that are running on top on their stack. With Quantum Armor Cloud Security you can harden your cloud security and monitor your activity in real-time.
Actionable Insights
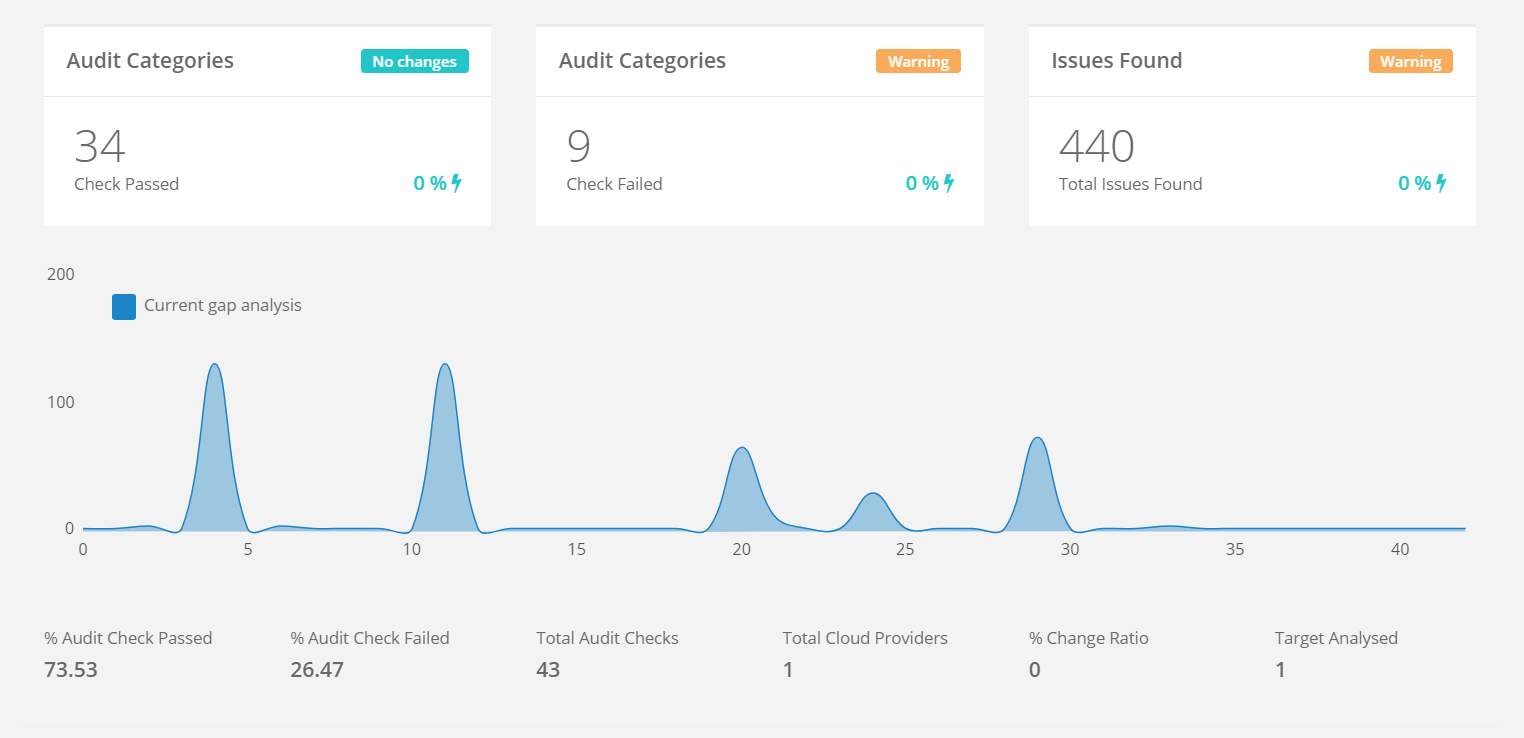
The first step in securing your virtual environment is to capture a clear and accurate picture of your cloud posture, and to see exactly what's visible to attackers.
To that end, Quantum Armor delivers daily notifications directly to your inbox to make sure you start your day with only the latest intelligence.
Concrete steps toward hardening your security are layed out, and common misconfigurations such as open S3 buckets or default credentials are flagged.
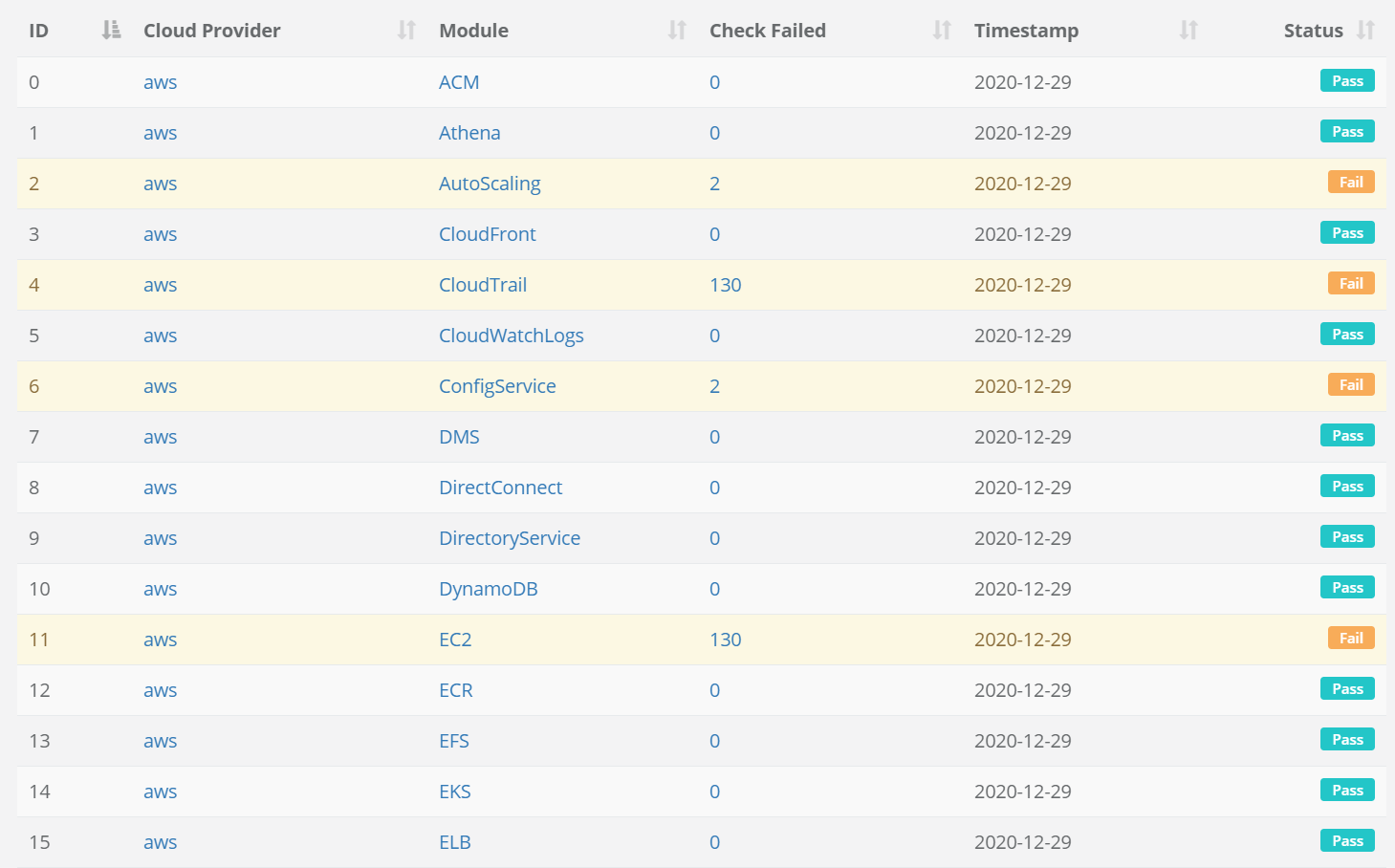
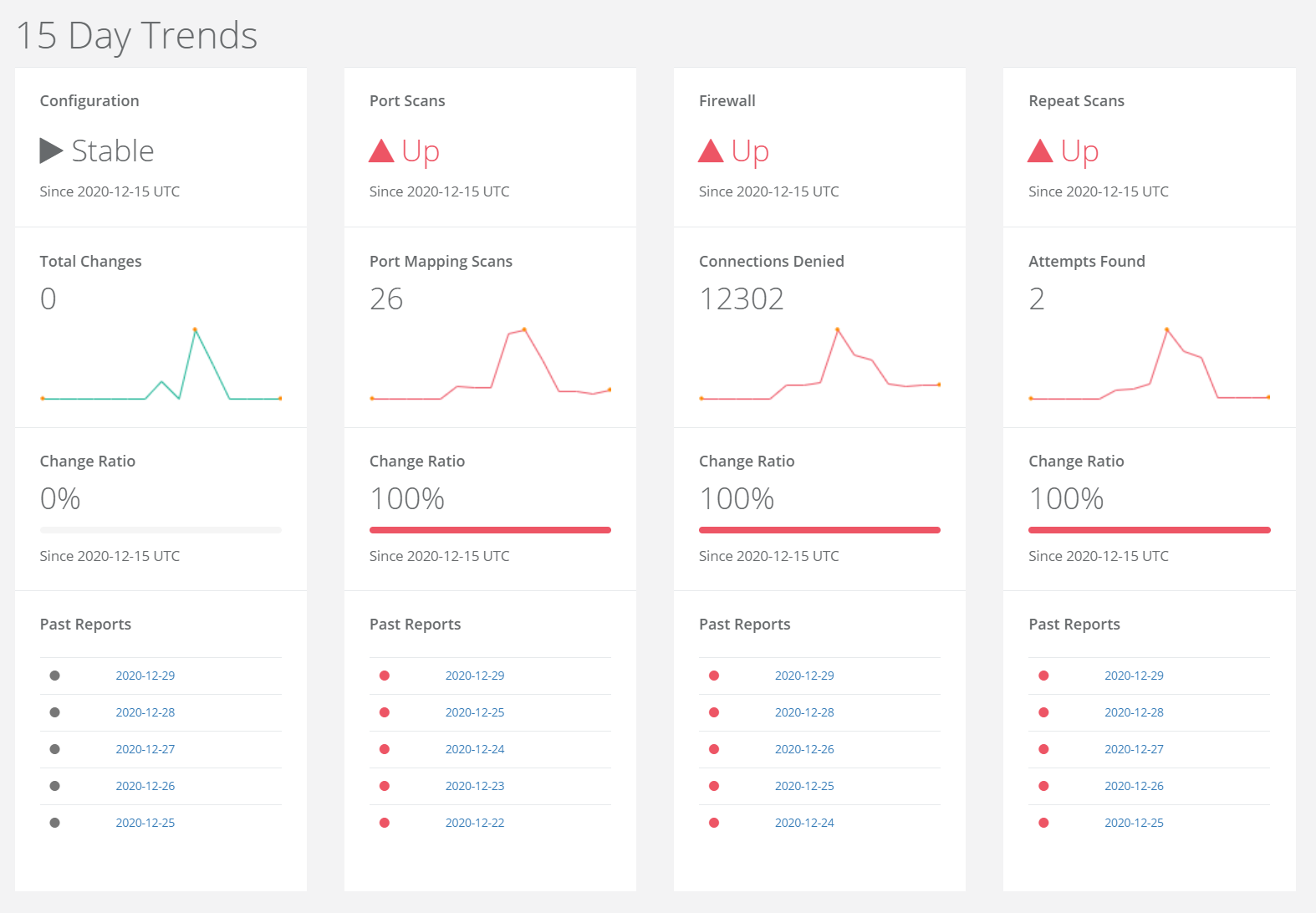
Observe Changes Over Time
With Quantum Armor, you can track your cloud security controls over time to spot attacks and identify trends.
In addition, Quantum Armor's artificial intelligence makes sense of millions of lines of logs to extract relevant information and determine the types of attack that your servers are most vulnerable to.
Identifying indicators of reconnaissance as early as possible will help you prevent attacks across your infrastructure before they have a chance to occur. These unique insights allow you to predict the future by looking at the past, and better prepare for imminent attacks.
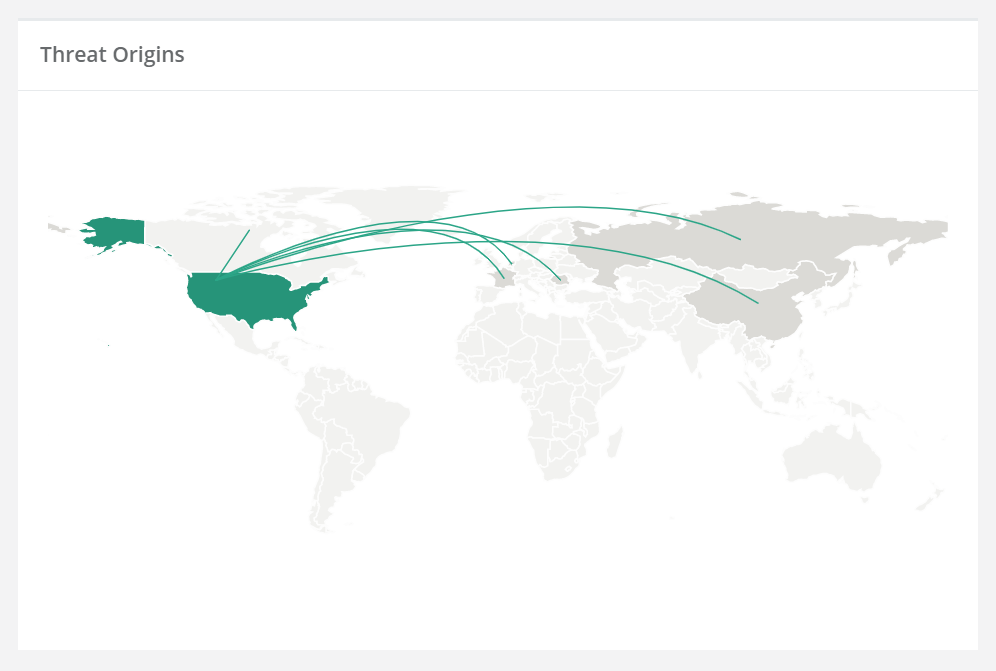
Threat Origins
A key component of your attacker's profile is their geopraphic location. Once a specific region or country can be identified, firewall rules and other defenses can be implemented to quickly and efficiently halt an attack in its tracks.
Geographically pinpoint the origin of attacks using Quantum Armor. Our proprietary Q-Traceback technology can even track down attackers behind VPN or proxy servers.
Obtain more information on your attacker's profile in order to defend your business and implement the proper response strategies.
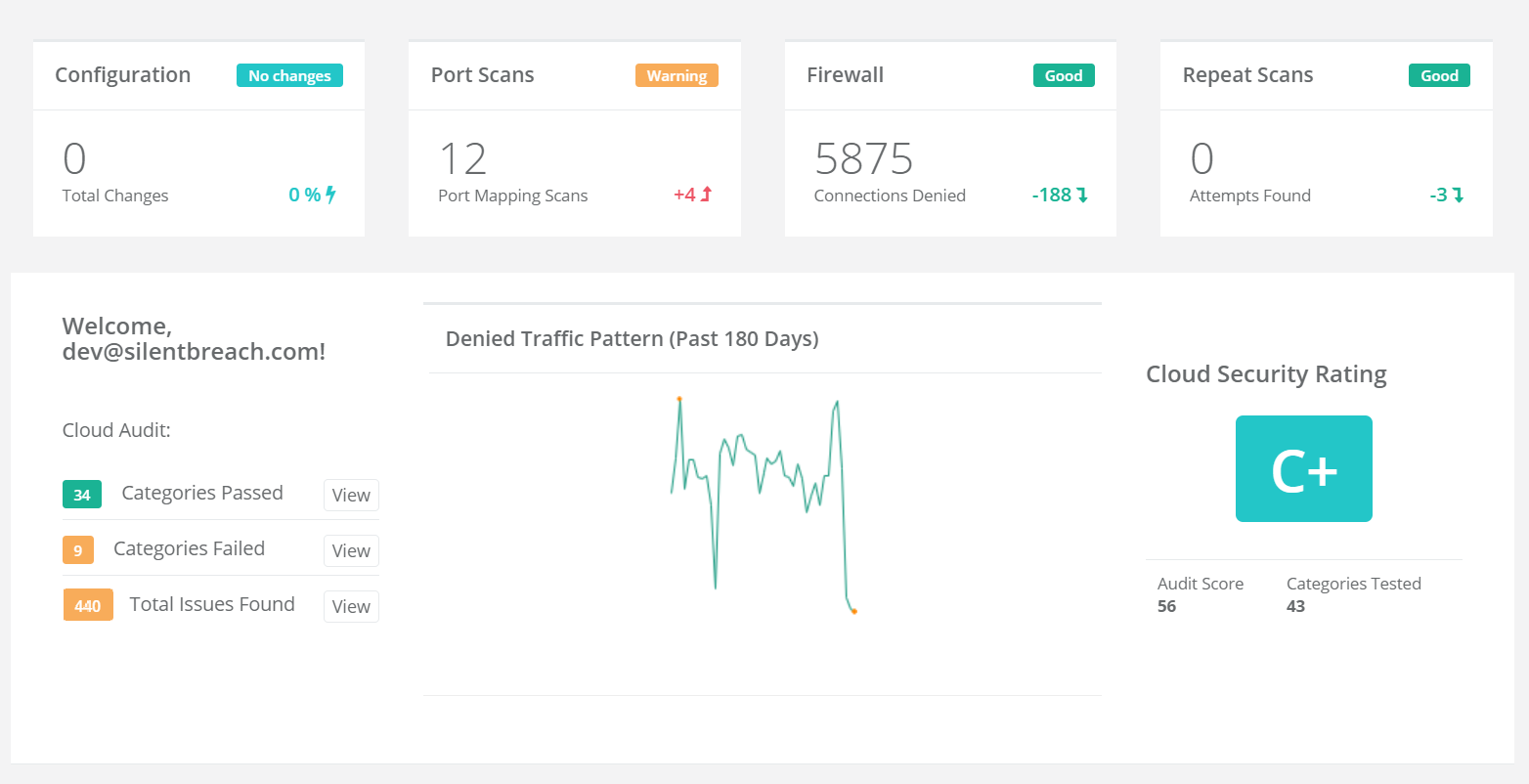
Integrated Dashboard
Concise and curated data helps your organization efficiently respond to cyber attacks. Quantum Armor condenses all of the information you need into a single user-friendly dashboard and organizes your attack surface into categories so that different teams can quickly identify and eliminate unwanted exposure.
Often, security engineers and business executives are forced to work with two different toolkits, each containing various unrelated tools. Quantum Armor bridges that gap by providing a single platform that is easily tailored to each stakeholder's needs and expertise.
With its instant Cloud Security Rating, you can quickly assess your overall cloud security posture and follow the tips to improve your rating and protect your business.
Use Cases
Cloud
Monitoring
Put your cloud security on autopilot and free up resources with Quantum Armor's daily reports sent right to your mailbox. Turn cloud security monitoring from a chore, to a given.
Compliance
Checks
Quantum Armor's cloud security engine can run pre-defined compliance runtime policies mapped to specific security standards, such as NIST, CIS level 1 and 2, PCI-DSS, GDPR and HIPAA.
Hybrid and Multi-Cloud Support
Quantum Armor partners with AWS, Azure, GCP, IBM Cloud, Oracle Cloud, and VMware to leverage native registries, orchestration, identity access management, monitoring and log collection.
Automated
DevSecOps
Add Quantum Armor into your development lifecycle to perform automatic daily audits. Receive real-time feedback whenever changes are detected in the cloud's attack surface or security configuration.
Omni-Infrastructure Monitoring
A single tool to monitor your on-premise infrastructure, web applications, IoT devices and cloud instances. Quantum Armor provides native integration with our attack surface monitoring platform.
Automated Log Analysis
Don't have time to comb through your cloud provider's logs? Let Quantum Armor highlight the important information in a user-friendly dashboard so you can focus on the real work.
Threat Intelligence Integration
Quantum Armor directly integrates threat intelligence from Malware Information Sharing Programs (MISPs) to identify any potentially known attack vectors in your cloud logs.
Web Application Security
Protect your company and your customers by adopting best-in-class cloud security right out of the gate with Quantum Armor's cloud auditing features and attack surface monitoring.