Ransomware Prevention
Leveraging threat intelligence to detect and diffuse your greatest risks.
A Growing Risk
During the last year, 22% of businesses were forced to pause operations due to ransomware, often for weeks at a time. While this may seem like business as usual, it is often catastrophic for those impacted.
Recent studies estimate that the average costs endured due to a ransomware breach sit at $4.5 million, in addition to lingering reputational damage.
At Silent Breach, we've analyzed hundreds of ransomware attacks to identify the key gaps and pressure points that hackers exploit during successful ransomware attacks.
In return, we've developed a flexible and robust set of audits, services, and tooling to help companies detect and mitigate 99% of ransomware attacks before they occur.
Ransomware Readiness Audit
The RRA is a comprehensive organizational-wide assessment that reviews your current preparedness, identifies your weakest links, and guides you toward mitigation.
The goal is to expose flaws and breaches in order to demonstrate how ransomware could be planted, or how your infrastructure and security team would cope with a real-life attack. Our award-winning experts are trained in both ransomware methodologies as well as tactical cybersecurity, to ensure that you'll be prepared against the very latest threats.
Deliverables include a final report with an executive summary, technical details, evidence that verifies the possibility of exploiting the discovered vulnerabilities, as well as recommended mitigation techniques.
Contact us today for a same-day custom quote.
Anti-Ransomware Threat Intelligence
Threat intelligence is a powerful anti-ransomware solution that continues to be significantly under-leveraged.
Our proprietary threat intelligence platform, Quantum Armor, provides access to curated, real-time, and targeted threat data from around the world, helping you fend off attacks before they occur.
Quantum Armor's NATO-backed intelligence is gathered from a variety of sources including OSINT (open-sourced intelligence), vulnerability databases, proprietary research, dark web monitoring, indicators of compromise, log analysis, and more.
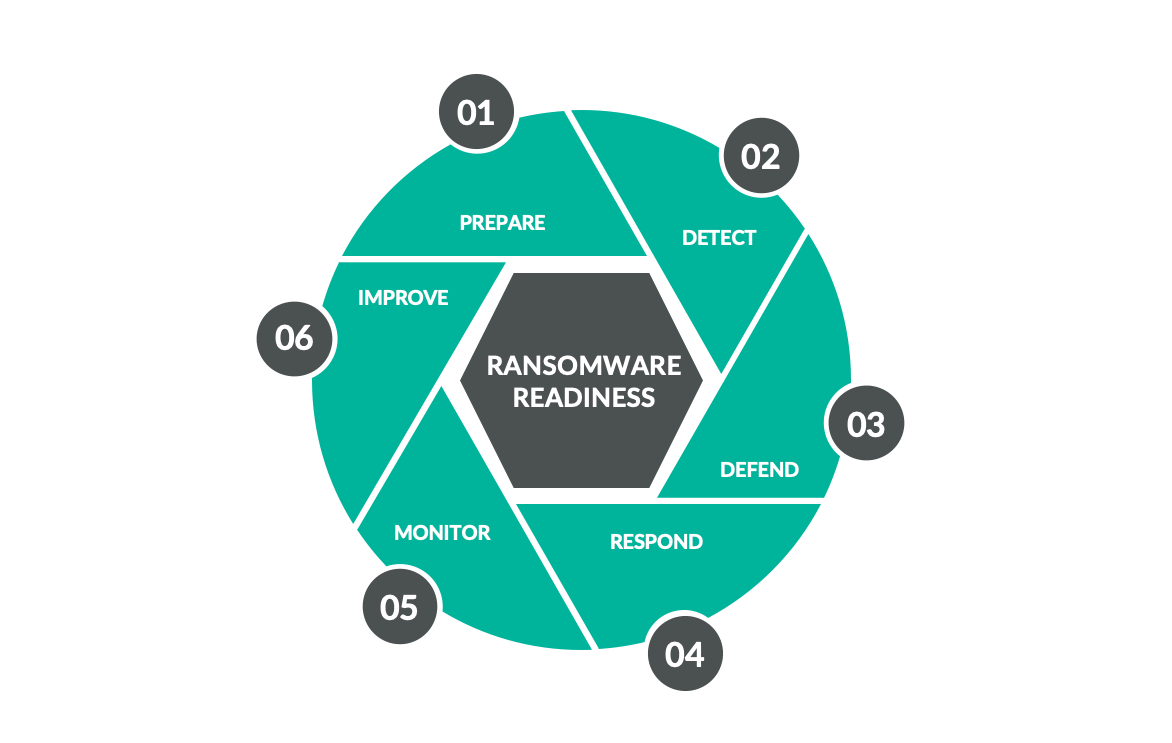
The Ransomware Threat Intelligence Lifecycle contains four stages:
Phase 1: Threat Profiling
Quantum Armor provides information on the tactics, techniques, and procedures (TTPs) currently being used by ransomware attackers, helping you identify and understand your real-world threats.
Phase 2: Threat Disruption
The first step in most ransomware attacks will be to search for company credentials that may have leaked onto the dark web due to a third-party breach. Alternatively, they may choose to launch a phishing attack (social hacking is used in 80% of successful breaches) by crawling the web for a list of company email addresses. Quantum Armor proactively identifies these security gaps, closing down most ransomware attack vectors before they get off the ground.
Phase 3: Threat Response
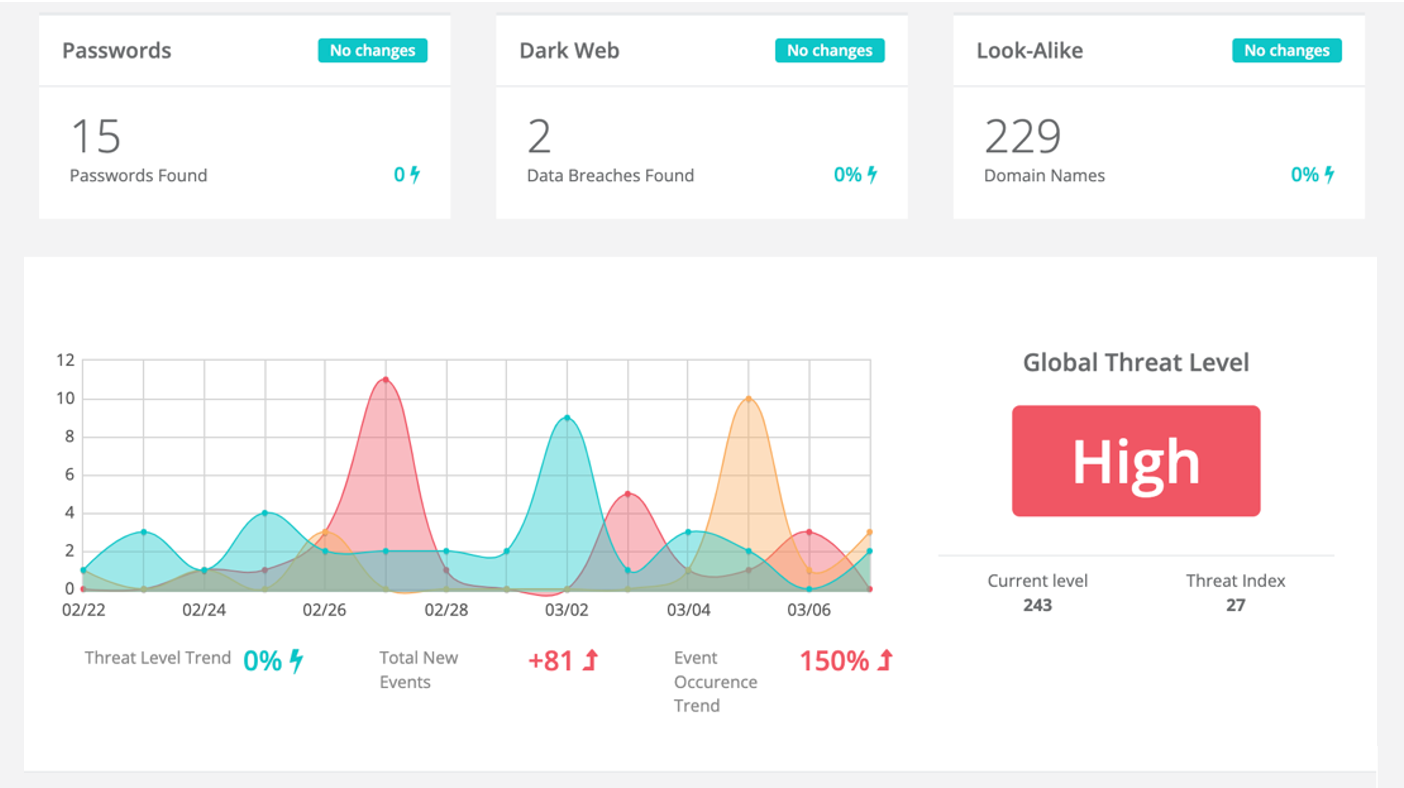
Threat intelligence can provide information on indicators of compromise (IoCs) associated with ransomware attacks, which can be used to detect and respond to attacks. For example, Quantum Armor instantly alerts you to any past or ongoing attacks against your company by flagging IoCs in your cloud logs, look-alike domains, as well as any sensitive data that's been leaked to the deep or dark webs.
Phase 4: Defense Strategy
Understanding your threat landscape helps you choose a proactive defense strategy to better protect your networks and data. Quantum Armor automatically groups your threats according to attack vector (e.g., social, infrastructure, or application), helping you visualize your posture and organize your efforts.
Our Ransomware Solutions
Ransomware
Readiness Audit
Our RRA methodology considers the entire ransomware kill chain from initial delivery through execution by reviewing your organization's existing maturity against the key anti-ransomware capabilities required to successfully mitigate an attack. This includes a strategic roadmap detailing a concrete path toward ransomware preparedness.
Penetration
Testing
Put your organization through the ultimate test and proactively identify gaps with a simulated ransomware attack conducted in a safe and controlled environment. A penetration test will let you know in no uncertain terms how your network will perform in the event of a real-world attack and measure the full extent of a potential fallout.
Threat
Intelligence
Quantum Armor runs 24/7 to closely monitor threat data, identify anomalies, and counteract developing cyberattacks in real time. All public data breaches are automatically reviewed to ensure they don't contain any sensitive data or credentials tied to your organization. Plans start at just $499 per month.
Managed Detection
and Response
Take advantage of our 24/7/365 incident response teams to immediately detect and respond to any ransomware incidents across your network. Silent Breach brings you the latest technology to beef up your cyber response at a fraction of the cost, letting you focus on what matters most: growing your business.
© Copyright Silent Breach. All Rights Reserved.