Managed Detection And Response
Never get caught unprepared.
Build Resilience
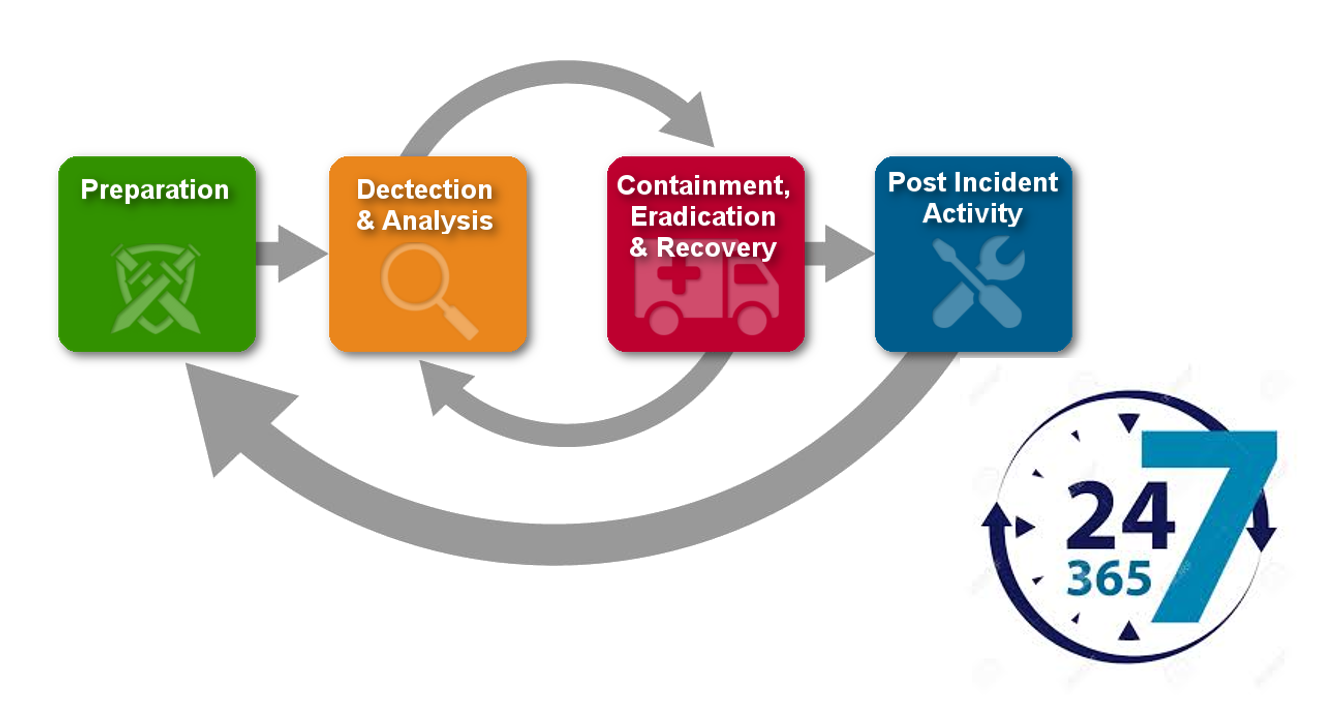
As everyone in the security industry knows, it is not a matter of if a data breach will occur, but when. With Silent Breach's suite of managed response solutions, you'll never get caught unprepared. Don't wait until you've been breached. Take advantage of our 24/7/365 response teams to immediately detect and respond to any cyber security incident across your network.
Silent Breach brings you the latest technology to beef up your cyber response at a fraction of the cost, so that you can focus on what matters most, growing your business.
Log Monitoring and SIEM Integration
Monitor your system and network logs 24/7/365 to detect attacks in real time. Our SIEM experts will notify your blue team whenever a threat is detected so you can take the appropriate measures.
Our Incident Response Program cuts down your Mean Time To Recovery (MTTR) to make sure your business is always up and running. Optimize your budget by having a full team of forensics experts and SOC analysts for a fraction of the cost.
Disaster Recovery
Business Continuity is critical for your company, but implementing a disaster recovery plan that can be executed in a timely manner and minimize downtime requires a lot of preparation.
Our team of experts is here to help you prepare a disaster recovery plan and execute it in case of a breach. Our incident response team can assist in rebuilding any part of your network that might have been damaged by an attack, or wiped out by ransomware.
Our automated backup tools will protect your business against most common ransomware attacks, including accidental loss of data and hardware failure, natural catastrophies and supply chain attacks.

Digital Forensics
Do you suspect that you've been breached and need assistance determining if you've been hacked? Let our forensics experts assist and collect court-admissible evidence. Our experts can retrieve both live and deleted data, internet history records, email communications or hidden log files using state-of-the-art forensic tools.
Our experts can also track down suspicious activities with cloud services such as Dropbox or Google Drive to determine if data exfiltration has occurred. Our network analysis tools can inspect network traffic to pin down any suspicious traffic.
Furthermore, our experts are trained in steganography and detecting Indicators of Compromise (IoC). Our threat intelligence research team shares trending malware with our forensics team to focus on known threats.