
3 Lessons Learned
Inside the Million Dollar Plot to Hack Tesla
According to FBI reports, Russian actors spent the summer of 2020 planning a cyber-attack against Tesla's systems.
Stay updated with all the latest news and announcements

3 Lessons Learned
According to FBI reports, Russian actors spent the summer of 2020 planning a cyber-attack against Tesla's systems.

Top Four Cybersecurity Threats
Several national security agencies have already confirmed foreign efforts to influence the US elections. Here are the top cybersecurity risks and their likelihood of success. ...
Guest Post
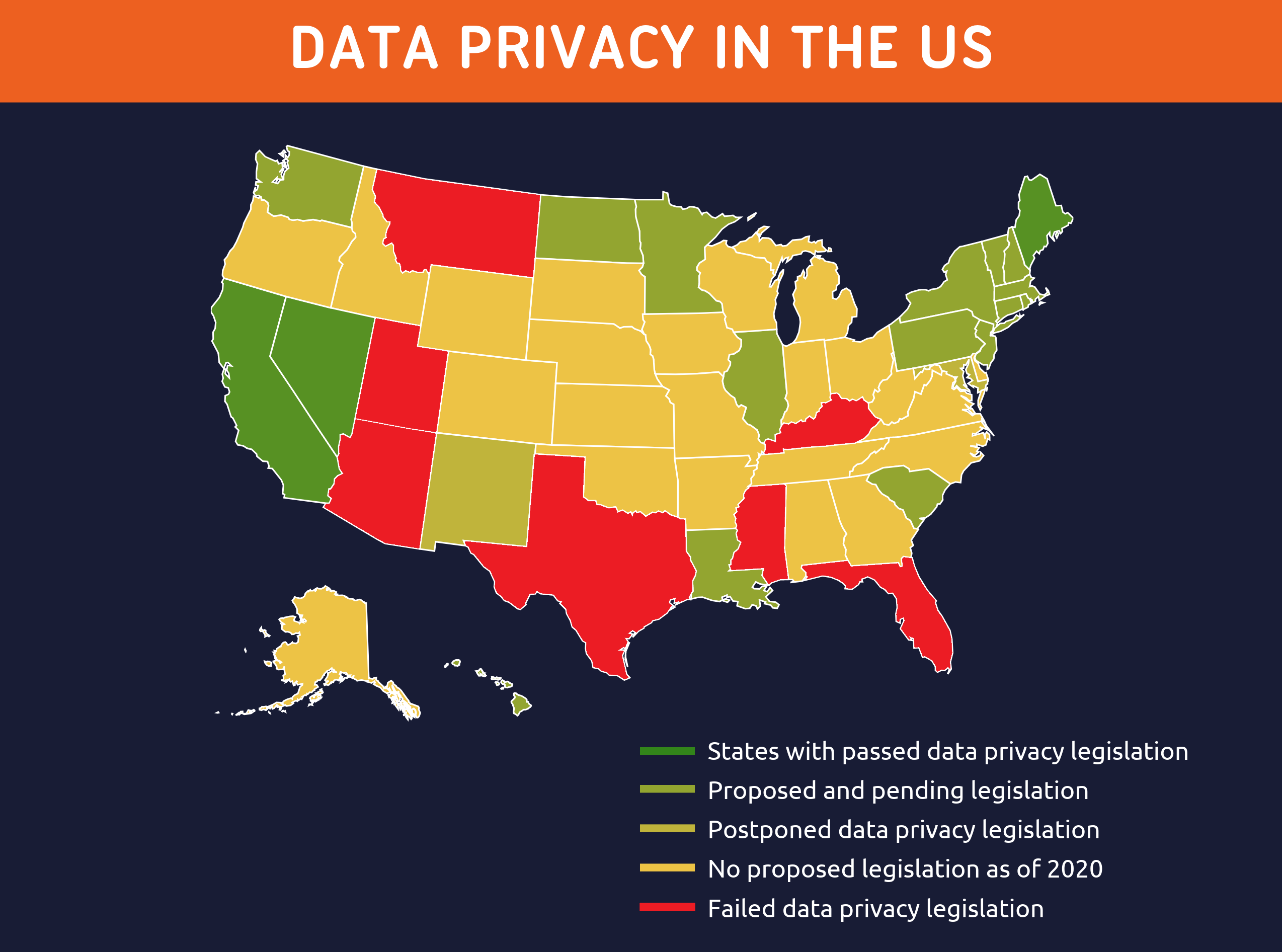
With rapid evolution of the digital world, data privacy protection has become a global trend for organizations, individuals and governments.

Cybersecurity Trends
Over the past few years, government entities around the world have banned public employees from installing TikTok on government phones. In the US, TSA personnel and soldiers a...

Lessons from COVID-19
While globalization has created economic and political opportunities for many, it is also contributed to the rapid spread of contagions such as COVID-19.

A side-by-side breakdown
As the greatest software rivalry of all time, emotions can run high. So we decided to create a non-partisan fact-based analysis of Android's and iOS's cybersecurity profile.

Cybersecurity Trends
The recent proliferation of social media platforms have provided hackers with a treasure trove of personal data on pretty much anyone in the world.

COVID-19 Update
Being secure means being prepared, so in this article we've broken down the major risks and key tips related to your cybersecurity posture under remote working conditions.

Executive Profile
Today we sit down with our Founder & CEO, Marc Castejon, to discuss his own professional journey, the current state of cybersecurity, and everything in between.

The Ponemon Institute
Every CISO faces the unique challenge of justifying a budget whose ROI is predominantly measured by what never happened.

Cybersecurity During a Global Crisis
The most vulnerable sector to cybersecurity attacks isn't Wall Street, the military, or even Silicon Valley. It's our healthcare system.
read more

Cybersecurity Trends
The WHO has labeled COVID-19 a global pandemic, setting off a wave of sweeping measures that have impacted not
only our physical lives, but our digital lives as well.
read more

The Ultimate Challenge
Following a wave of devastating breaches, many firms are looking for better strategies to manage cybersecurity risks. One highly effective exercise is the PenTest.

Cybersecurity Trends
At long last, the World Economic Forum has finally come to recognize cybersecurity as the "second most concerning risk for doing business globally over the
next 10 years," signaling a growing recognition within the business community of the importance of their CISOs and the challenges they face.
read more
It's official
Airports are (in)famous for their lengthy physical security checks, but how do they rank in terms of cybersecurity? A team of security researchers recently set out
to find out once and for all by assessing the current state of cybersecurity at the world's 100 largest airports. Here's what they found: read more

A Guide to Ransomware Payments
It's no secret that 2019 was in many ways the Year of Data Breaches. While many cybercriminals steal data in order to mount further attacks or to sell it on the Dark Web, ransomware
attackers are unique in that they make a simple offer: pay a ransom and everything will go back to normal.
read more

Four Lessons from FIC 2020
The theme of FIC 2020 was Putting Humans at the Heart of Cybersecurity, so it's no surprise that social hacking
remained a hot button topic throughout the three-day conference. read more

Cybersecurity Trends
The World Economic Forum just released their 2020 Global Risk Report, a compilation of research conducted by global risk consultants and financial analysts
defining the major business risks facing the markets in both the short and long term. read more

Cybersecurity Trends
While encryption technologies, systems, and standards have become incredibly secure over the past decade, it has become increasingly clear that the the largest cybersecurity threat to nearly any organization is its people. ...
Silent Breach in the press
announcement
Silent Breach in the press
© Copyright Silent Breach. All Rights Reserved.