
Cybersecurity Trends
Common Blockchain Security Flaws
Blockchain has ushered in a new era of transparency, cryptography, and decentralization. However, there is still a long way to go to overcome glaring security challenges.
Stay updated with all the latest news and announcements

Cybersecurity Trends
Blockchain has ushered in a new era of transparency, cryptography, and decentralization. However, there is still a long way to go to overcome glaring security challenges.

And what caused them
Blockchain projects soared 700% in 2021. In the process, they've become extremely attractive targets for hackers across the globe.

Guest Post
Businesses now understand how important it is to protect their customers' and brands' personal data. However, retaining top cybersecurity talent isn't as easy as it sounds.

Cybersecurity News
On July 6th, the heads of the FBI and MI5 met in London to deliver an unprecedented joint warning regarding China's "game changing" cyber offensives.

Guest Post
Although coined way back in the mid-90s, there are many reasons why the metaverse is being touted as the future of the internet.
In 5 Steps
As budgets tighten and teams shrink, cybersecurity leaders will be facing an impossible challenge: how to accomplish more with fewer resources.

Including attack phases and timeline
The Russian invasion of Ukraine was arguably the first war in history to combine the full power of an advanced kinetic and cyber arsenal.
Guest Post
A recent report by Gartner names attack surface expansion as the leading cybersecurity trend to watch for in 2022.

Cybersecurity Trends
MFA has proven itself to be one of the most impactful cybersecurity innovations in recent decades. But it's still not enough.
In Four Steps
With 95% of the internet hosted on the Deep and Dark Webs, companies now have a valuable opportunity to leverage this data for positive purposes. ...

Cybersecurity Trends
A string of crypto thefts and security breaches have caused some to question the overall security of a rapidly growing industry.

Cybersecurity Trends
While 2021 presented some of the greatest security challenges in decades, it has also prompted government and industry leaders to prioritize cybersecurity.

Cybersecurity Trends
In many ways, 2021 was the year that global supply chains were pushed to their limits, both physically and digitally.
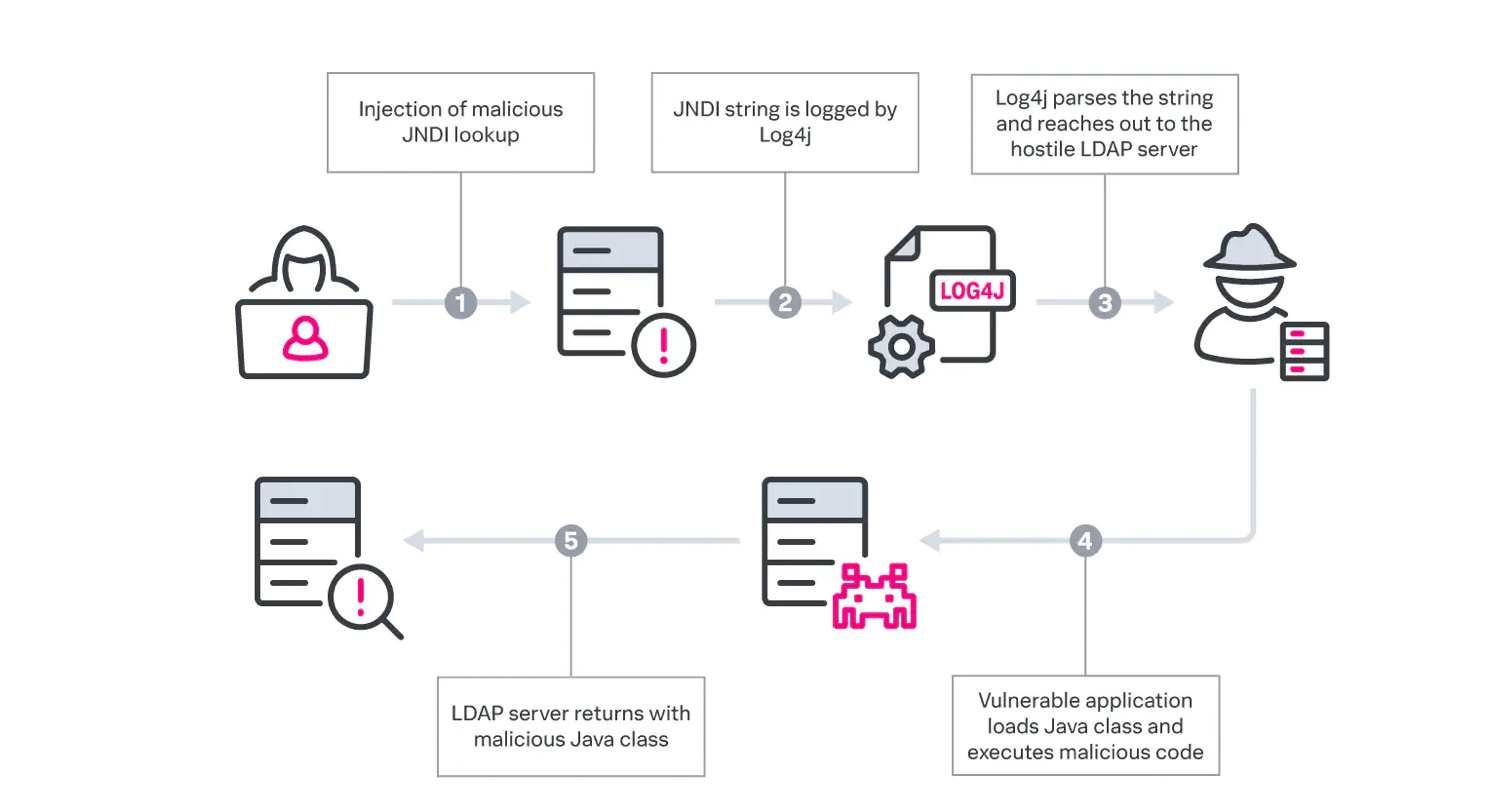
Silent Breach Labs
To help companies detect and mitigate the Log4j vulnerability, Silent Breach is offering a free advisory service. Contact us to learn more.

Top Three Risks
While the global supply chain has only recently fallen into crisis, the digital supply chain has been under stress for years.

And what to do about it
The strategy is simple. Wait until nearly all employees are away from the office. A long weekend, like Thanksgiving or July 4th, will do just fine. An extended break like Chri...

Cybersecurity News
The cybersecurity sector was met with a number of important victories, wrapping up what could be its best week in recent months.

Cybersecurity Trends
As the newest addition to the due diligence process, cyber audits come in all shapes and sizes. Here are the main 4 components, along with accompanying case studies.

Cybersecurity Trends
Back when WhatsApp released their new data-sharing policies, public outrage over privacy concerns caused users to flock to rivals like Signal and Telegram nearly overnight.
Silent Breach in the press
announcement
Silent Breach in the press
© Copyright Silent Breach. All Rights Reserved.