
Cybersecurity Trends
Best Penetration Testing Providers in North America
Penetration testing has become an essential part of the modern cybersecurity strategy, and for good reason.
read more

Cybersecurity Trends
CVE-2025-21391: Elevation of Privilege in Windows Storage
On February 11, 2025, Microsoft disclosed CVE-2025-21391, an elevation of privilege (EoP) vulnerability affecting Windows Storage.
read more

Cybersecurity Trends
How to Choose an MDR Service for SMEs
As cyber threats continue to grow in sophistication, many SMEs are turning to Managed Detection & Response services to strengthen their security posture.
read more

Cybersecurity Trends
CVE-2025-22222: Credential Exposure in VMware Aria
On January 31, 2025, VMware disclosed CVE-2025-22222, a credential exposure vulnerability affecting VMware Aria Operations (formerly vRealize Operations Manag...
read more

Cybersecurity Trends
Guide to Cybersecurity Compliance in Singapore
With rising threats and increasing regulatory scrutiny, staying compliant with Singapore’s security laws is both a necessity and a competitive advantage.
read more
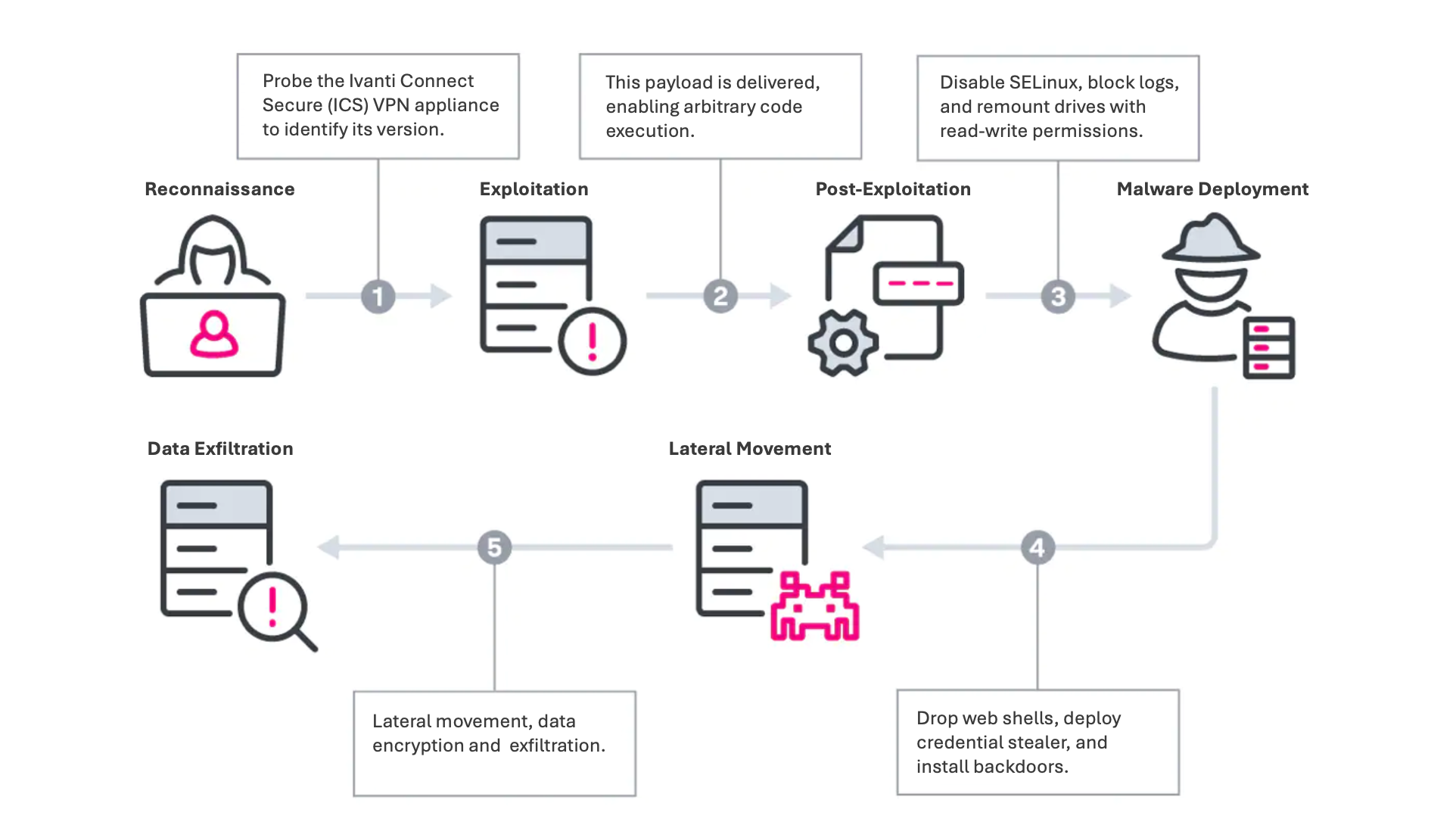
Cybersecurity Trends
Critical Vulnerability Alert: CVE-2025-0282 in Ivanti Products
On January 8, 2025, cybersecurity researchers from SecureIntel Labs disclosed a critical vulnerability, CVE-2025-0282, affecting Ivanti Connect Secure, Policy...
read more

Cybersecurity Trends
China's Cybersecurity Sector: Key Players and Future Outlook
China's cybersecurity market has seen rapid growth, fueled by the country's accelerated digital transformation and increasingly complex cyber threats.
read more

Cybersecurity Trends
Cybersecurity Measures Behind the 2024 U.S. Elections
This year, public and private sector efforts to protect the election have grown more sophisticated.
read more

Cybersecurity Trends
6 Proven Strategies CISOs Use to Increase Organizational Buy-In
Time and again, CISOs tell us that their number one challenge is a lack of organizational buy-in.
read more

Cybersecurity Trends
Why Transportation Is So Attractive To Hackers
In recent weeks, two cyberattacks in particular have filled the headlines: an internet shutdown at major UK train stations and the MoneyGram hack.
read more

Cybersecurity Trends
The State of Cybersecurity in Commercial Aviation
In an era where planes are essentially flying data centers, the need for robust cybersecurity is more pressing than ever.
read more
Cybersecurity Trends
NIST Releases First Post-Quantum Encryption Recommendations
This is not hype. Within a decade, quantum computing will transform everything from weather forecasting to theoretical physics.
read more

Cybersecurity News
Highlights from Black Hat 2024
As usual, this year's Black Hat conference drew thousands of security researchers, professionals and enthusiasts to the sandy desert oasis of Las Vegas.
read more

Cybersecurity Trends
The Costs and Benefits of SOC 2 and ISO 27001 Compliance
SOC 2 and ISO 27001 provide a structured approach to managing sensitive information and ensuring data security, but they also come with their own set of costs...
read more

Cybersecurity Trends
The Secret Service's Cyber Capabilities
While best known for their bodyguards and snipers, the U.S. Secret Service has accumulated an impressive suite of advanced cyber capabilities.
read more

Cybersecurity Trends
Top Five Malware Strains in 2024
Hackers are leveraging AI to develop new malware strains at an alarming rate. Researchers estimate that over 1,500 new variants are introduced daily.
read more

Cybersecurity News
Top 5 Mistakes When Pursuing Cybersecurity Compliance
At a time when cyber threats loom large, achieving cybersecurity compliance with standards like ISO 27001 or SOC 2 is not just a regulatory requirement but a ...
read more

Cybersecurity News
GISEC Global 2024 Recap
The latest round of GISEC Global took place in Dubai last week, bringing together thousands of industry experts, vendors and customers over three days.
read more

Cybersecurity News
Evaluating the Biden Administration's Cybersecurity Impact
With elections fast approaching, it's important to review the current administration's performance regarding their cybersecurity goals and campaign promises.
read more
Load More
Silent Breach in the press
Silent Breach Breaches Department of Defense (DoD) Network
announcement
Silent Breach joins the Cyber Security Tech Accord
Silent Breach in the press
Silent Breach's mission to protect millions of devices
© Copyright Silent Breach. All Rights Reserved.